Assessments
Security Assessments
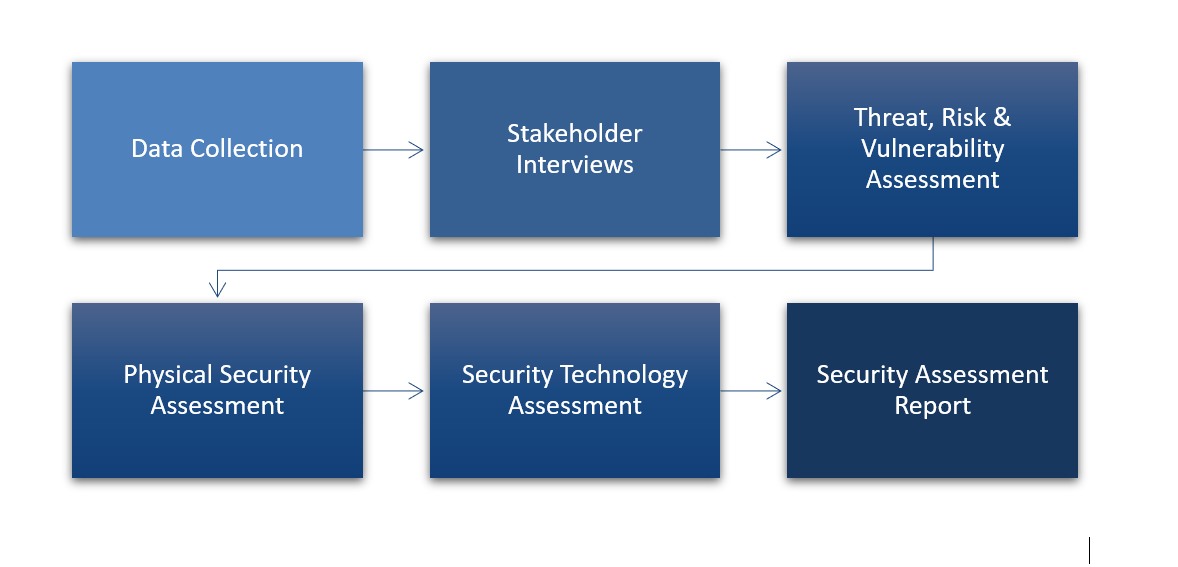
Our process has been used to perform hundreds of assessments over the past 35 years. Our depth and breadth of experience combined with best practices and the latest security standards, allows us to develop a more balanced assessment.
Data Collection & Stakeholder Interviews
We work with key stakeholders to gather all information necessary to ensure a thorough understanding of your site, operations, procedures and potential risks.

Threat, Risk & Vulnerability Assessments
After reviewing and prioritizing risks and threats, we provide an analysis of the likelihood of specific threats, as well as an evaluation of the vulnerability of each site.
- Identify, assess and prioritize threats
- Measure and quantify vulnerabilities
- Site specific risk analysis
- Recommended countermeasures
Physical Security Assessments
Through detailed site inspections, we evaluate the security infrastructure, hardware, governing policies, program and operating procedures of the site.
Security Technology Assessments
This assessment identifies the appropriate technologies needed to protect the human and physical environment of the site, including:
- Access Control Systems & Intrusion Detection
- IP Video Recording Systems, Video Cameras
- Video Analog to IP Conversion
- Perimeter Protection & Gate Access
Assessment Report & Improvement Plan
Our report identifies critical assets and threats and evaluates existing security measures to identify potential weaknesses and areas for improvement. The report also includes compliance recommendations per CPTED, C-TPAT, FISMA, CFATS, OSHA, NFPA, FEMA, and ASIS regulations.